Have you ever been prompted with a “User account does not have permission” while running a task or modifying an object in Windows 10? If yes, it means that the account that you are logged in from does not have the required rights to perform the task. Certain levels of privilege are required to perform advanced tasks and execute commands.
This article discusses what user privileges are, how they are categorized, and everything you need to know about the different types.
Table of Contents
What is a User Account
A user account is a location on a computer to store user data including username, password, user profile and other data related to the user.
Windows 10 supports multiple User Accounts for different people, where each of them can have their own user account. This helps seclude their information from one another, as well as keep one user from altering the data of another user. Apart from the data on the shared drives, their personal data is stored separately, and so are their application configurations and settings.
Generally speaking, there are two types of user accounts on Windows 10:
- Local account
- Microsoft account
The local account is the one created on the hosting computer and is not associated with any domain or email. Whereas the Microsoft account is directly associated with a Microsoft ID.
Although these are the two main categories of types of accounts, there are options within these categories to choose from. These further subcategories decide the role of each account and are referred to as Groups.
These user accounts are further classified into a number of groups, out of which some of the significant ones are:
- Administrative Users
- Standard Users
- Power Users
- Child Users
These categories/groups define the rights and privileges each user account shall have, and are entirely independent of the fact whether its a Local account, or a Microsoft account. The user accounts are then added to each group, where they inherit the level of access from these Organizational Units (OUs).
Let’s dig in further as to how these user account types illustrate the user privileges.
Understanding user privileges
The level of access a user account has is determined by which group the user belongs to. Each user can belong to one group or more at the same time. The set of rules applied to the group will then apply directly to the users within that particular group.
The privileges defined by these groups let a user modify certain settings and control their Operating System, or prompts them that they do not have the required access and must sign in using the appropriate account.
Standard user
A Standard User, also known as Default User, can pretty much control their own account and not alter the settings, nor can they access the data from another user’s account. This is best used if you want to limit user access on a computer that you own. The following are some of the examples these accounts can do:
- Change their account’s password, or remove it.
- Customize the theme and backgrounds on their profile.
- View and edit their personal files, or folders in shared drives only.
A standard user cannot install system level software.
Administrative user
An Administrative User can manage their whole computer, such as create or delete user profiles, access system files, and registries, manage applications, set group policies, etc. All in all, Administrative accounts have more power and control compared to other users. Some of their key features are:
- Alter settings affecting all user accounts.
- Create, delete, or manage all user accounts.
- Change system security settings that affect all users.
- Access and edit files and folders of other users as well.
Upon fresh installation of Windows 10, a user account already exists by the name Administrator, which cannot be deleted. It can only be renamed or disabled. By default, this account is disabled and needs to be manually enabled for use.
As Administrative users have more power and control over the computer, it is recommended to not make every user an Administrator, and keep a close circle in this group. It is recommended to only let trusted people in as Administrators.
Power user
A Power User has the same privileges as Administrators, except that they do not have access to view live subscriptions or billing information. Other than that, they also have full control of the computer.
These types of accounts are recommended for IT professionals in an organization that needs to manage the systems, without knowing the financials of it.
Child user
Child User accounts, as the name suggests, are primarily for families to keep control and restrict what their child does on their computer. They can limit screen time, or only allow age-appropriate content on this user. Moreover, it prevents them from accidentally deleting system files or moving them about. The following are a few key features of this type of account:
- Monitor internet browsing history, as well as application and game use.
- Block unwanted websites, or allow specific websites only.
- Allow the use of only age-appropriate applications and games.
- Manage subscriptions and set a spending limit.
Backup operators
Backup Operators group users can backup and restore system files and folders regardless of ownership or permission of those files. Backup operators can:
- Backup and restore files and folders to the entire system.
- Revert files and folders to an older state.
- Backup operators can start or stop TSM Scheduler Service (an automated service to take regular backups).
Cryptographic operators
Cryptographic operators can manage operations on the system regarding encryption. Some examples of their functions are:
- Create, delete, or manage VPNs.
- Configure Cryptography Next Generation (CNG) on Windows 10.
- Can edit the cryptographic settings in the IPsec policy of the Windows Firewall.
Hyper-V administrators
Members of this group have the right to manage hyper-V virtual machines and their settings, regardless of their ownership. Some critical tasks they can perform are:
- Create, remove, or delete Hyper-V virtual machines on the local computer.
- Change the network, storage, and RAM configurations of virtual machines running on Hyper-V.
- Access virtual machines to modify them from the inside.
- Restart or reset virtual machines.
IIS_IUSRS account
This group is primarily for users willing to view or modify any files in the foot folders of the system. Users belonging to the group IIS_IUSRS can:
- Modify and edit any files belonging to any website hosted locally.
- Use the application pool identity to access file content.
Network configuration operators
The users belonging to this group can manage the network settings of the complete system, which may affect other users as well. Some of the key features of this group are:
- Modify TCP/IP configurations of all ports on the computer.
- Enable or disable network adapters.
- Monitor and control network traffic
- Limit network usage
Remote Desktop users
As the name suggests, the users in this group can manage who uses this feature, and who is allowed to connect to the local computer. Some of the key features are:
- View remote desktop history/ events.
- Allow specific users or computers to remotely access the system.
- Restrict or allow specific users to remotely access other computers from this PC.
How to change user privileges
As mentioned earlier, the privileges are controlled by the group policies. Hence, moving a user to the appropriate group will alter their rights and level of access. Here is how you can manage an existing user in a group:
- Open up the Computer Management Console by typing in compmgmt.msc in Run.
- Expand Local Users and Groups from the left pane, and then click Groups.
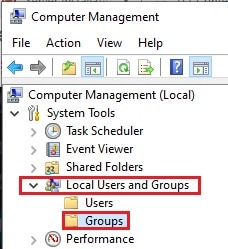
- In the right pane, double-click the group you want to add the user to.
- In the Group Properties window, click on Add to add new users to the group, or click on the user and click Remove to remove them from the group.
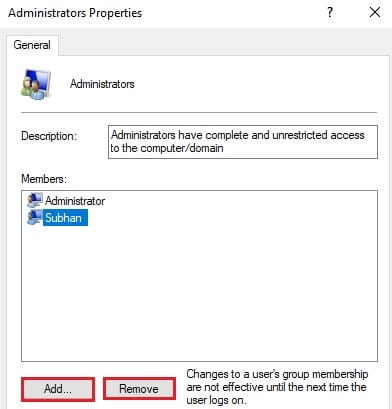
Once you have added a new user to the group, their privilege level will change accordingly. If you remove them from a group, they will lose the rights associated with the group.
Which policy takes precedence in case of conflict?
As we mentioned earlier, a user account can be a member of more than one group. Since both groups have different policies applied, how will the computer determine what policy the account should follow?
If a user is a part of more than one group, then the rules, privileges, and rights of those groups will all apply to the user account. However, there can be a conflict of privileges. For example, one group allows access to the internet, while the other one blocks it. How does the computer determine which policy will take precedence?
One feature of Windows 10 is the Group Policy Editor. This utility let’s us modify the Group Policy Objects (GPOs) that apply directly to the Organisational Units. Meaning, whatever policy is applied to the GPOs affects the OUs. Since the OUs are at the top of the hierarchy and are processed last, they are the ones that take precedence and finalize the applicable policy of a user account.
We hope that this article cleared up some of your concepts and how user privileges work.
