DNS-over-HTTPS (Secure DNS) is a new technology that aims to make web browsing secure by encrypting the communication between the client computer and the DNS server.
This new Internet standard is being widely adopted. The adoption list includes Windows 10 (Version 2004), Android 9 Pie, Google Chrome, Mozilla Firefox, Microsoft Edge, Opera and Vivaldi to name a few.
In this article, we will discuss the advantages and disadvantages of DNS-over-HTTPS and how to enable this protocol in your devices.
We will also discuss how to test if DoH is enabled for your devices or not.
Let’s begin.
Table of Contents
A simple explanation of DNS-over-HTTPS and how it works
DNS-over-HTTPS (DoH) is a protocol for encrypting DNS queries between your computer and the DNS Server. It was first introduced in October 2018 (IETF RFC 8484) with a goal of increasing user security and privacy.
Traditional DNS servers make use of DNS port 53 for communication while DNS-over-HTTPS makes use of the HTTPS port 443 to communicate securely with the client.
Please note that although DoH is a security protocol, it does not prevent ISPs from tracking your requests. It simply encrypts the DNS query data between your computer and the ISP to prevent issues like spoofing, man-in-the-middle attack etc.
Let’s understand this with a simple example.
Here is how DNS works:
- If you want to open the domain name itechtics.com and request it using your browser.
- Your browser sends a request to the DNS Server configured in your system e.g., 1.1.1.1.
- The DNS recursive resolver (1.1.1.1) goes to the root servers of the top level domain (TLD) (.com in our case) and asks for the name servers of itechtics.com.
- Then the DNS server (1.1.1.1) goes to the name servers of itechtics.com and asks for the IP address of the itechtics.com DNS name.
- The DNS server (1.1.1.1) carries this information to the browser and browser connects to itechtics.com and gets a response from the server.
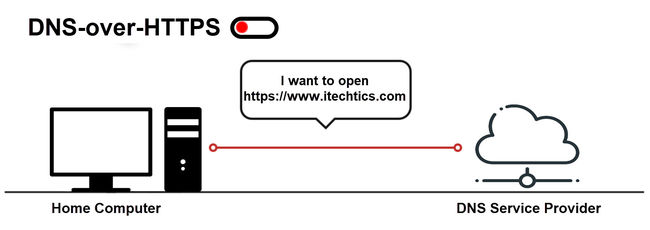
All this communication from your computer to the DNS server to TLD DNS servers to the name servers to the website and back is done in the form of simple text messages.
That means anyone can monitor your web traffic and easily know what websites you’re opening.
DNS-over-HTTPS encrypts all the communication between your computer and the DNS server making it more secure and less prone to man-in-the-middle and other spoofing attacks.
Let’s understand this with a visual example:
When DNS client sends DNS queries over to the DNS server without using DoH:
When a DoH client uses the DoH protocol to send DNS traffic to the DoH enabled DNS server:
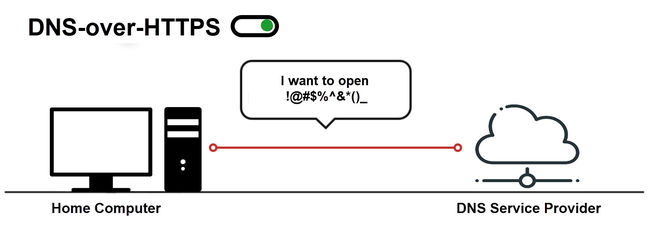
Here you can see that the DNS traffic from the client to the server is encrypted and no one knows what the client has requested. The DNS response from the server is also encrypted.
Pros and Cons of DNS-over-HTTPS
While DNS-over-HTTPS will slowly replace the legacy DNS system, it comes with its own advantages and potential problems. Let’s discuss some of them here.
DoH does not enable complete privacy of the user
DoH is touted as the next big thing in user privacy and security, but in my opinion, it is only focused on user security and not on privacy.
If you know how this protocol works, you will know that DoH does not prevent ISPs from tracking user DNS requests.
Even if the ISP is not able to track you using the DNS because you’re using a different public DNS provider, there are a lot of data points which are still open to the ISPs for tracking. For example, Server Name Indication (SNI) fields and Online Certificate Status Protocol (OCSP) connections etc.
If you want more privacy, you should check out other technologies like DNS-over-TLS (DoT), DNSCurve, DNSCrypt etc.
DoH does not apply to HTTP queries
If you are opening a website that does not operate using SSL, the DoH server will fall back to the legacy DNS technology (DNS-over-HTTP) also known as Do53.
But if you are using secure communication everywhere, DoH is definitely better than using the bare metal old and insecure DNS technologies.
Not all DNS servers support DoH
There are a large number of legacy DNS servers that will need to be upgraded to support DNS-over-HTTPS. This will take a long time for wide-spread adoption.
Until this protocol is supported by most DNS servers, most users will be forced to use the public DNS servers offered by large organizations.
This will lead to more privacy issues as most of the DNS data will be collected at a few centralized locations around the world.
Another disadvantage of early adoption of DoH is that if a global DNS server goes down, it will trip the majority of the users using the server for name resolution.
DoH will be a headache for enterprises
While DoH will improve security, it will be a headache for enterprises and organizations that monitor their employees activities and use tools to block NSFW (not safe for work) parts of the web.
Network and system admins will have a hard time coping with the new protocol.
Does using DNS-over-HTTPS slow down browsing?
There are two aspects of DoH to look for when testing the performance against the legacy Do53 protocol:
- Name resolution performance
- Webpage loading performance
Name resolution performance is the metric we use to calculate the time it takes for the DNS server to give us the required server IP address of the website we want to visit.
Webpage loading performance is the actual metric of whether we feel any slowdown when we are browsing the Internet using DNS-over-HTTPS protocol.
Both of these tests were performed by samknows and the final result is that there is negligible difference in performance between DNS-over-HTTPS and the legacy Do53 protocols.
You can read the complete performance case study with stats at samknows.
Here are the summary tables for each metric we defined above. (Click on the image for larger view)
Name resolution performance test

Webpage loading performance test

How to enable or disable DNS-over-HTTPS on Windows 10
Windows 10 Version 2004 will come with DNS-over-HTTPS enabled by default. So once the next version of Windows 10 is released and you upgrade to the latest version, there will be no need to enable DoH manually.
However, if you are using Windows 10 Insider Preview, you will need to enable DoH manually using the following methods:
Using Windows Registry
- Go to Run –> regedit. This will open Windows Registry Editor.
- Open the following registry key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters - Right-click on Parameters folder and select New –> DWORD (32-bit) Value.
- Name it EnableAutoDoh.
- Set the value of EnableAutoDoh entry to 2.

You will need to restart the computer for the changes to take effect.
Please note that this change will take effect only when you are using the DNS servers that support DNS-over-HTTPS. Below you will find a list of public DNS providers that support DoH.
Earlier versions of Windows 10 including version 1909 and 1903 do not support DoH by default.
Using Group Policy
I’m keeping this section for future use. Right now, there are no group policy rules for DNS-over-HTTPS. We will fill in the steps when Microsoft makes them available for Windows 10 Version 2004.
Using PowerShell (Command line)
I’m keeping this section for future use. If Microsoft provides a way to enable or disable DoH using the command line, we’ll list the steps here.
How to enable or disable DNS-over-HTTPS in your browsers
Some applications support bypassing the system configured DNS server and use DNS-over-HTTPS instead. Almost all modern browsers either already support DoH or will support the protocol in the near future.
Enable DNS-over-HTTPS in Google Chrome
- Open Google Chrome and go to the following URL:
chrome://settings/security - Under Advanced Security, toggle on Use secure DNS.
- After enabling secure DNS, there will be two options:
- With your current service provider
- With Google’s recommended service providers
You can select whatever suits you. The second option will over-ride your system’s DNS settings.

To disable DoH, simply toggle the Use secure DNS settings to off.
Enable DNS-over-HTTPS in Mozilla Firefox
- Open Firefox and go to the following URL:
<a href="about:preferences" class="rank-math-link">about:preferences</a> - Under General, go to Network Settings and click on the Settings button. Or simply press the E keyboard key to open settings.
- Scroll to the bottom and check Enable DNS over HTTPS.
- From the drop-down, you can choose your preferred secure DNS server.

Enable DNS-over-HTTPS in Microsoft Edge
- Open Microsoft Edge and go to the following URL:
edge://flags/#dns-over-https - Select Enabled from the drop-down beside Secure DNS lookups.
- Restart the browser for the changes to take effect.

Enable DNS-over-HTTPS in Opera Browser
- Open the Opera browser and go to Settings (Alt + P).
- Expand Advanced on the left-hand menu.
- Under System, toggle on Use DNS-over-HTTPS instead of the system’s DNS settings.
- Restart the browser for the changes to take effect.

The secure DNS settings didn’t take effect until I disabled the Opera’s built-in VPN service. If you are having issues with enabling DoH in Opera, try disabling the VPN.
Enable DNS-over-HTTPS in Vivaldi Browser
- Open the Vivaldi browser and go to the following URL:
vivaldi://flags/#dns-over-https - Select Enabled from the drop-down beside Secure DNS lookups.
- Restart the browser for the changes to take effect.

How to enable DNS-over-HTTPS in Android
Android 9 Pie supports DoH settings. You can follow the steps below to enable DoH on your Android phone:
- Go to Settings → Network & internet → Advanced → Private DNS.
- You can either set this option to Auto or you can specify a secure DNS provider yourself.

If you are unable to find these settings on your phone, you can follow the steps below:
- Download and open QuickShortcutMaker app from the Google Play Store.
- Go to Settings and tap on:
com.android.settings.Settings$NetworkDashboardActivity
This will take you directly to the network settings page where you will find the secure DNS option.
How do you check if you are using DNS-over-HTTPS?
There are two ways to check whether DoH is enabled properly for your device or the browser.
The easiest way to check this is by going to this cloudflare browsing experience check page. Click the Check My Browser button.
Under Secure DNS, you will get the following message if you are using DoH:
You are using encrypted DNS transport with 1.1.1.1
If you are not using DoH, you will get the following message:
You may not be using secure DNS.
Windows 10 Version 2004 also gives a way to monitor port 53 packets in real-time. This will tell us if the system is using DNS-over-HTTPS or the legacy Do53.
- Open PowerShell with administrative privileges.
- Run the following commands:
pktmon filter remove
This removes all active filters, if any.pktmon filter add -p 53
This adds port 53 to be monitored and logged.pktmon start --etw -m real-time
This starts with real-time monitoring of port 53.
If you see a lot of traffic being shown in the list, this means the legacy Do53 is being used instead of DoH.
Please note that the above mentioned commands will only work in Windows 10 Version 2004. Otherwise, it will give you an error: Unknown parameter ‘real-time’
List of Name Servers that support DoH
Here is the list of DNS service providers that support DNS-over-HTTPS.
| Provider | Hostname | IP Address |
| AdGuard | dns.adguard.com | 176.103.130.132 176.103.130.134 |
| AdGuard | dns-family.adguard.com | 176.103.130.132 176.103.130.134 |
| CleanBrowsing | family-filter-dns.cleanbrowsing.org | 185.228.168.168 185.228.169.168 |
| CleanBrowsing | adult-filter-dns.cleanbrowsing.org | 185.228.168.10 185.228.169.11 |
| Cloudflare | one.one.one.one 1dot1dot1dot1.cloudflare-dns.com | 1.1.1.1 1.0.0.1 |
| Cloudflare | security.cloudflare-dns.com | 1.1.1.2 1.0.0.2 |
| Cloudflare | family.cloudflare-dns.com | 1.1.1.3 1.0.0.3 |
| dns.google google-public-dns-a.google.com google-public-dns-b.google.com | 8.8.8.8 8.8.4.4 | |
| NextDNS | dns.nextdns.io | 45.90.28.0 45.90.30.0 |
| OpenDNS | dns.opendns.com | 208.67.222.222 208.67.220.220 |
| OpenDNS | familyshield.opendns.com | 208.67.222.123 208.67.220.123 |
| OpenDNS | sandbox.opendns.com | 208.67.222.2 208.67.220.2 |
| Quad9 | dns.quad9.net rpz-public-resolver1.rrdns.pch.net | 9.9.9.9 149.112.112.112 |
Although DNS-over-HTTPS make the web more secure and should be implemented uniformly across the web (like in case of HTTPS), this protocol is going to give nightmares to sysadmins.
Sysadmins need to find ways to block public DNS services while enabling their in-house DNS servers to use DoH. This needs to be done to keep the current monitoring equipment and restriction policies active across the organization.
If I have missed anything in the article, please let me know in the comments below. If you liked the article and learned something new, please share it with your friends and on social media and subscribe to our newsletter.





2 comments
Dan
Windows 10 does not support DNS over HTTPS.
cam
This is for DNS over TLS–android doesn’t natively support DNS over HTTPS.