The “550 SPF Check Failed” error is usually seen in a bounce-back email, which is an automated reply from the mail server when you send out an email. This error is quite common, as email security and authentication are now being taken seriously by all organizations and individuals.
If this error shows up in your email, it means that the email you sent out has not been delivered to the recipient. This error normally occurs because there is an issue with authentication at the sender’s end, and rarely at the receiver’s side.
In this guide, we are going to discuss what this error means, why it occurs, and the measures you can take to fix it. Before that, a little about SPF.
Table of Contents
What is an SPF check
Sender Policy Framework (SPF) is one of the few email authentication methods. It functions through a list of servers that are allowed to send emails on behalf of your domain, and that list is stored in a DNS SPF record, which is a TXT record maintained on a DNS.
It is a security check in place that makes sure that only the servers in the list can send emails on your behalf. This blocks spoofers from manipulating the envelop header of an email and using your domain’s name to send spam emails.
Suppose an SPF check is configured correctly, and a hacker attempts to use your domain’s name to impersonate you. In that case, the receiving email server will quickly detect it by performing a DNS lookup, and verifying that the server that sent that email is not on the allow list, hence blocking the email.
What does the “550 SPF Check Failed” error mean
The “550” in the bounce-back email is the error code. It can be used to look up the error on the web and troubleshoot the issue. The rest of the error statement implies that the SPF validation check failed, and the email that was sent did not pass the SPF check. This then results in the email not being delivered.
The email can fail the SPF check due to several different reasons, which have been discussed below. However, the core reason is, that the domain in the envelop header, or the “return path”, is not listed in the SPF record, and therefore, the SPF check failed. However, there can be multiple reasons why the domain was not found in the SPF record, even if it was sent from a legitimate domain.
Causes for the SPF Check Failed error
Incorrect SPF record configuration
To correctly create and use an SPF record, it must be configured correctly. this means that the qualifiers, mechanisms, and values in the record should be correct, and the syntax of the overall record should meet the standards.
Moreover, you must make sure that the SPF record is a TXT type, or type 16 record. Anything else would make it invalid, and for the mail servers, the SPF record would not exist.
To learn how to correctly configure an SPF record, refer to our detailed guide.
Spoofed email header
Rarely the case, but it may be possible that the email header that you are sending out is spoofed. This is normally done by hackers to impersonate someone legitimate from the organization, but it might be possible that your “return address” is being spoofed to something else without you knowing about it.
Incomplete SPF record
An SPF record must contain all the servers that are authorized to send emails on the domain’s behalf. If you miss a server, it may block your emails from being delivered to the recipient, causing a similar bounce-back email.
Therefore, make sure that all servers are mentioned inside the SPF record, and that all DNSs are returning the same SPF records.
You can check this using our Email Security & Deliverability Checker, which performs several DNS lookup checks as well as other industry best practice checks.
The emails are being relayed
If there are several hops between your email server and its final destination server, as it is when you are using relays, they won’t be included in your domain’s SPF record and may be the likely reason for a bounce-back error.
This happens because email forwarding causes the email header information to change in transit, pointing the return path address to the intermediary’s domain when a message travels via an intermediate server. The receiving server might not accept this external relay as a valid sender, which would result in a “550 SPF Check Failed” error.
SPF exceeds the 10 lookup limit
According to the documentation by the Internet Engineering Task Force (IETF) – an organization that defines the rules and standards for email authentication protocols – the SPF lookup limit is limited to only 10. This means that a maximum of 10 SPF DNS lookup queries are allowed per SPF record.
This rule has been implemented to tackle DOS attacks. A Denial of Service (DoS) or a Distributed DoS attack is where a single, or multiple compromised devices are used to generate and send data packets to a single server or endpoint, making it extremely slow, or in some cases, completely incapable of performing its regular functions.
If an SPF record lookup exceeds this limit, you can see a bounce-back email stating “SPF Check Failed”. Therefore, you need to make sure that your SPF record is configured correctly and within the limit.
To learn more about how the lookup count works and the methods to fix it, refer to our detailed guide here.
Incorrect MX records
If your MX record is not pointing to the right server, your email might not be delivered to the intended recipient. If it points to the incorrect mail exchange server, then you might see a “550 SPF Check Failed” bounce-back email.
How to fix the “550 SPF Check Failed” error
Correctly configure the SPF record
The first thing you can do to fix the error is to make sure that your SPF record is configured correctly. To begin, check out whether the current configuration is right or not. For that purpose, you can use our Email Security & Deliverability Checker.
Simply put your domain’s name in the field and click Analyze, then wait and check whether your SPF record, as well as other essential configurations, are set up correctly.
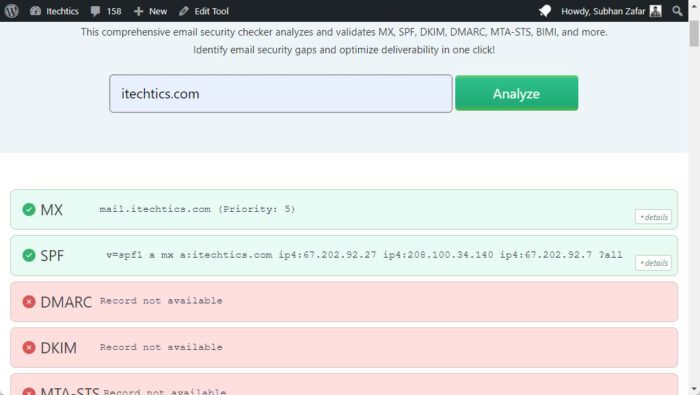
If it shows that the SPF record is not configured correctly, then proceed to make the necessary changes.
Here is a complete guide to learn what an SPF record should look like:
While correcting the SPF record, make sure to beware of these common errors:
- Extra spaces before or after the string
- Misspellings
- Extra dashes
- Uppercase characters
- Additional commas and spaces
Verify MX record
As mentioned earlier, incorrect MX records can also cause the said error. Therefore, make sure the DNS MX record is pointing toward the correct mail exchange server.
Add forwarders and vendor IP to SPF record
If you are using a third-party service for emails, but your DNS records are your own, make sure to include the vendor’s IP addresses in the SPF records.
Email service providers have established particular criteria for the alignment of your sending sources. For example, if you use Google Workspace, then you can find a guideline for setting up the DNS records and adding Google’s servers to the SPF record to set up mail authentication correctly.
Takeaway
It is one thing to not configure any security measures for your emails and domain, but an entirely different thing to configure it incorrectly.
As you can see, you can end up running into errors or missing emails that were actually authentic and should have landed in your inbox by configuring the email security protocols incorrectly. One such error is the “550 SPF Check Failed” error, which occurs when the email you sent out did not pass the SPF test.
Thankfully, the receiving mail server was configured to send out a bounce-back error message, letting you know that the email was not delivered, after which you can use this guide to mitigate the issue.
