Windows Remote Desktop isn’t always the most reliable method to access machines remotely. People often use other modes to remotely access them as well, and Chrome Remote Desktop is one of those famous modes.
However, when connecting to remote devices using Chrome Remote Desktop, you not only require an identification code, but also a Personal Identification Number (PIN) code. This PIN code is used to authenticate that you are authorized to access that device.
A PIN code is essential so that no unauthorized personnel can connect to a device and make any unauthorized changes or hack it. The person on the remote device needs to inform you of that PIN code for you to be able to connect to it. However, if you have a device that is only on a local network, or one that does not require that level of security, you can remove the PIN and connect to it directly.
Table of Contents
This article discusses 2 ways you can disable the PIN authentication step while connecting to a remote computer using Chrome Remote Desktop.
Disable PIN Authentication In Google Chrome Remote Desktop
Disable PIN authentication in Chrome Remote Desktop using Group Policy
By default, Windows 10 Group Policy does not include any policies to manage Google Chrome. However, you can add Google Chrome Policy Template to Windows 10 to configure Chrome accordingly. Once done, you can use it to disable PIN authentication for Chrome Remote Desktop.
Launch the Group Policy Editor by typing in gpedit.msc in Run and then navigate to the following location using the left pane:
Computer Configuration -> Administrative Templates -> Classic Administrative Templates -> Google -> Google Chrome -> Remote access
On the right, double-click “Enable or disable PIN-less authentication for remote access hosts.”
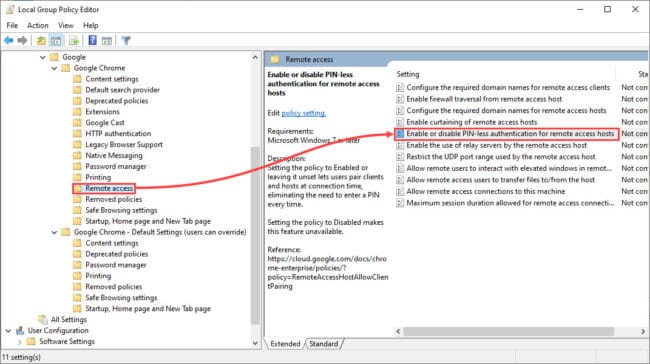
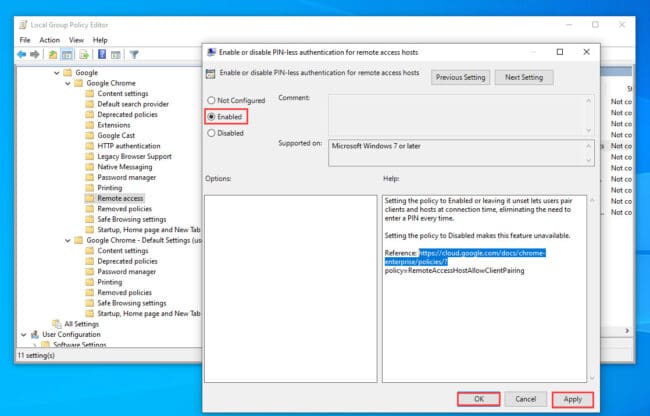
In the pop-up window, select the Enabled radio button and then click Apply and Ok to allow users to authenticate a remote session without having to enter a PIN code.
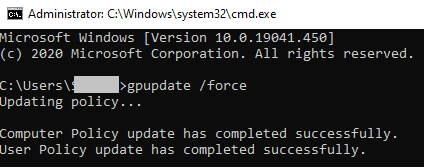
Now all that is left to do is enforce the changes by typing in gpupdate /force in the Command Prompt.
Now you can connect to this PC remotely with just its access code without having to enter a PIN code.
if you feel like re-enabling the PIN requirement for Chrome Remote Desktop, all you need to do is return the same policy within the Group Policy Editor and this time select the Disabled radio button.
Disable PIN authentication in Chrome Remote Desktop using Registry Editor
You can also disable PIN authentication using just the Registry Editor. This method can be adopted if you are running Windows 10 Home, as it does not come with Group Policy Editor, or if you do not want to add the Google Chrome Policy Template to your OS.
However, we should warn you that any wrong manipulation of the system registries could be fatal for your operating system. Therefore we recommend that you create a system restore point before proceeding forward.
Launch the Registry Editor by typing in regedit in Run and then paste the following link in the address bar for quick navigation:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies
Right-click Policies, expand New, then click Key from the context menu. Name this new Key as Google. Now right-click Google and create a new Key named Chrome. Once done, right-click Chrome, expand new, and now click DWORD (32-bit) Value. Name this DWORD as “RemoteAccessHostAllowClientPairing.”
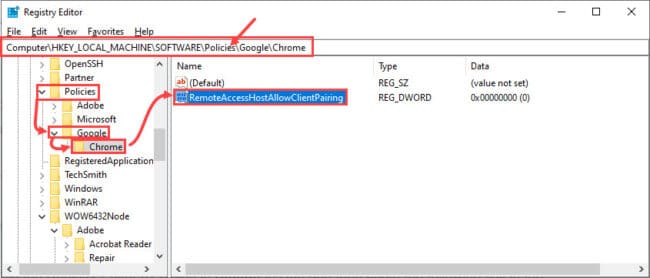
Now double-click the new DWORD just created and set its Value Data to 1 and click Ok.
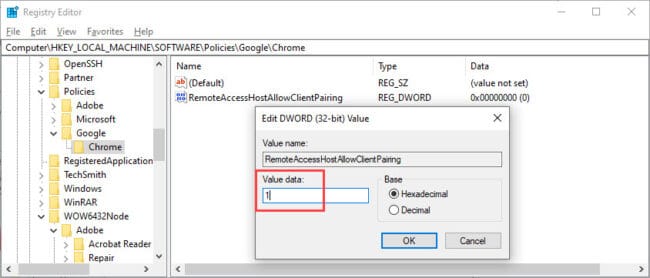
Once done, reboot the computer for the changes to take effect.
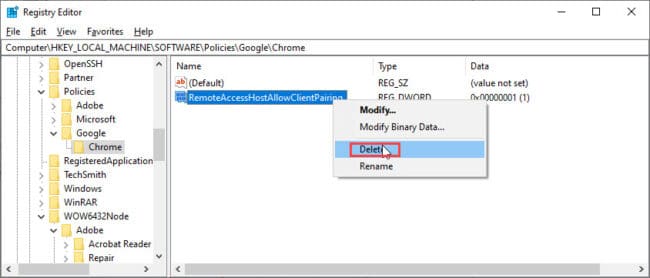
You can now connect to this PC using Chrome Remote Desktop without having to enter a PIN code. However, if you feel like implementing the PIN code again in the future, simply delete the DWORD or the keys created using the Registry Editor and restart the device.
Closing words
Although having a PIN-less authentication mechanism may be faster and convenient, it may not always be the best choice. Therefore, we suggest that you only remove the PIN requirement for Chrome Remote Desktop where the device is not connected to the internet, it does not have any sensitive information, and it is not connected to a network of other devices. Otherwise, unauthorized access to one device can result in infiltration of an entire network, or you could lose sensitive and personal information.



