All communications between different devices happen using a specific protocol. One such authentication protocol is “NTLM.” NTLM is an old technology originally introduced with Windows NT 3.1. However, the current modern Windows operating systems, like Windows 11, still support this technology, and for good reason.
However, since the NTLM authentication technology is old and outdated, hackers tend to hijack the data packets in this protocol, making your usernames and passwords vulnerable.
Whether you’re a sysadmin using Windows Server, or a regular person with a Windows client operating system, you can make your network secure by monitoring, and even blocking the NTLM authentication protocol.
In this article, we cover in detail what the NTLM authentication protocol is, why it is used, why it is still supported, and how to monitor any apps or programs that still use it, so it can be blocked.
Table of Contents
What is NTLM Authentication
NTLM is an authentication protocol used to verify that a user is who he/she claims to be. This is verified using your credentials, of course. When a PC inside an Active Directory decides to access another computer, the credentials are first sent to the Domain Controller using the NTLM protocol, after which the access is either denied or granted.
When the credentials are traveling through the network, a hacker can easily gain access to the packets which isn’t very difficult in the modern age, and the NTLM technology is (almost) obsolete.
Before NTLM, there was another authentication protocol known as “LM.” That, of course, was even weaker than NTLM. With NTLM, Microsoft released the NTLMv1 initially, but improved its security and released NTLMv2. Both of these are insufficient to counter the threats of modern technology. This is why it will be wise to monitor and block this technology from being used at all.
Why is NTLM Still Supported by Windows
Even though NTLM is an outdated technology, the latest version of Windows still supports it. This is to counter any compatibility issues.
People still running older applications and servers may need to use the NTLM protocol for authentication purposes, as their environment does not allow the use of its successor; “Kerberos” – a more secure and modern authentication protocol.
Ideally, all networks should be using Kerberos for authentication as it is more secure, the NTLM is still supported for the people who are running older environments.
Why is NTLM Authentication a Threat
The NTLM authentication protocol uses hashing – an encryption mechanism – to envelop the actual username and password. However, even this approach is not secure according to modern times. If a hash code is intercepted by a hacker, they can’t decipher it, but they can use the entire hash to authenticate with the Domain Controller. The DC will then authenticate the imposters instead of authenticating you, the actual person who generated the request in the first place.
Because of this threat, it is important to check and block the NTLM authentication protocol and replace it with Kerberos, if possible.
How to Monitor NTLM Protocol
When we talk about monitoring the NTLM traffic, you can find out which apps or ports are sending or receiving NTLM packets on your PC. This can be done on both Windows Servers as well as Windows client OS.
The NTLM traffic can be monitored through different methods:
Monitor NTLM using Group Policy
Microsoft provides a group policy that can be used to verify NTLM authentication in AD domains. In addition, it shows NTLM authentication requests to domain controllers. Moreover, the policy also offers different settings that are discussed in the following steps.
Perform these steps to start monitoring NTLM traffic on your network:
-
Open the Group Policy editor by typing in “gpedit.msc” in the Run Command box.
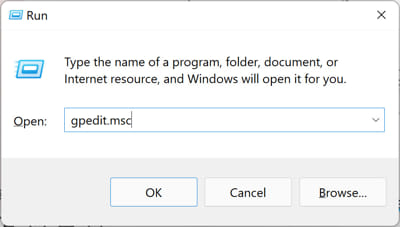
Open the Group Policy editor -
Navigate to the following from the left pane:
Computer Configuration >> Windows Settings >> Security Settings >> Local Policies >> Security Options
-
In the right pane open the policy “Network security: Restrict NTLM: Audit NTLM authentication in this domain.”
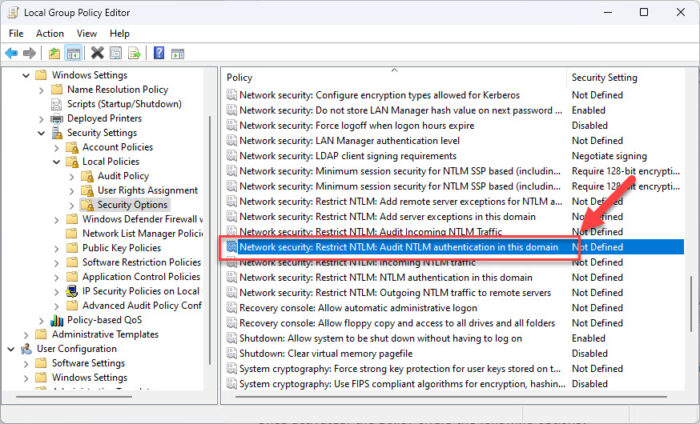
Open NTLM audit policy -
Now select one of the following options from the drop-down menu:
- Enable for domain accounts to domain servers – logs events related to NTLM authentications for domain accounts on DCs.
- Enable for domain accounts – Records events for NTLM logon attempts that use domain accounts
- Enable for domain servers – Log NTLM authentications on all servers in the domain
- Enable all (recommended option) – Records NTLM pass-through authentications from servers and for the accounts
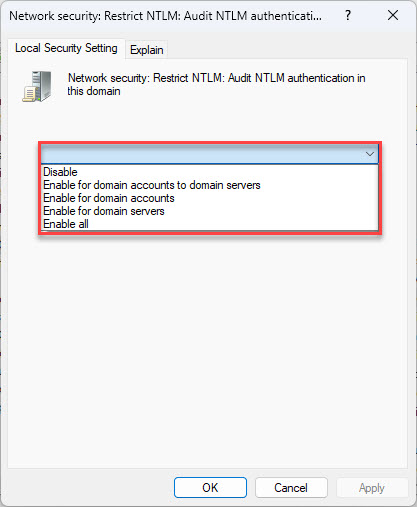
Set policy to start monitoring NTLM traffic -
Click Apply and Ok.
-
Run the following cmdlet in an elevated Command Prompt to enforce the policy changes:
GPUpdate /Force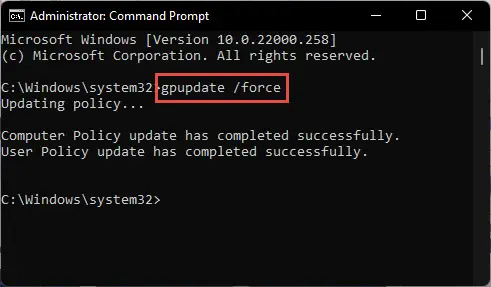
Enforce policy changes
Now, the computer will start recording and logging the NTLM traffic and save the logs inside the Event Viewer. Here is how you can view the logs in the Event Viewer:
-
Open the Event Viewer by typing in “eventvwr.msc” in the Run Command box.

Open the Event Viewer -
Navigate to the following from the left pane:
Applications and Services Logs >> Microsoft >> Windows >> NTLM >> Operational
-
Here, all events about the NTLM protocol will be displayed.
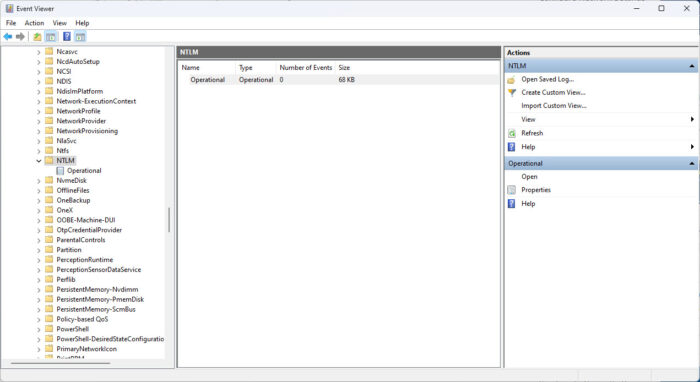
View NTLM logs inside the Event Viewer
Another quicker method to view all NTLM logs is from Windows PowerShell.
Monitor NTLM using PowerShell
NTLM traffic logs can be checked using PowerShell as well. However, you will still need to enable the Group Policy as discussed above.
Use the following command to fetch the NTLM events in an elevated PowerShell:
Get-WinEvent -LogName "Microsoft-Windows-NTLM/Operational"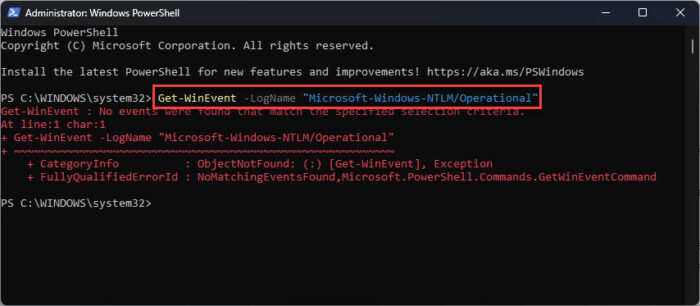
Monitor NTLM using Logon Events
You can also find out which applications are using NTLMv1 by monitoring the success of logon events on a Domain Controller. Of course, to monitor this, a Group Policy needs to be configured. Follow these steps:
-
Open the Group Policy editor by typing in “gpedit.msc” in the Run Command box.

Open the Group Policy editor -
Navigate to the following from the left pane:
Computer Configuration >> Windows Settings >> Security Settings >> Local Policies >> Audit Policy
-
In the right pane open the policy “Audit account logon events.”
-
Select “Success” and then click Apply and Ok.
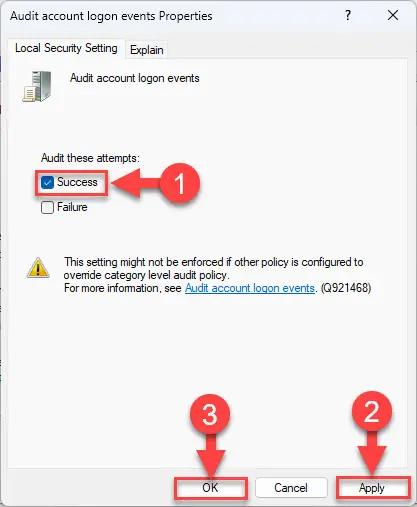
Audit logon events -
Run the following cmdlet in an elevated Command Prompt to enforce the policy changes:
GPUpdate /Force
Enforce policy changes
Now, you can check the Event Viewer again for the logon events to identify the applications still using the NTLM protocol. These events will have the event ID “4624.”
These are all the methods to find out and monitor which apps are using the NTLM protocol. Let us now see how to disable/block NTLM authentication on your domain.
How to Disable NTLM Authentication
NTLM authentication can be blocked on your domain if you perform the following steps on the Domain Controller:
-
Open the Group Policy editor by typing in “gpedit.msc” in the Run Command box.

Open the Group Policy editor -
Navigate to the following from the left pane:
Computer Configuration >> Windows Settings >> Security Settings >> Local Policies >> Security Options
-
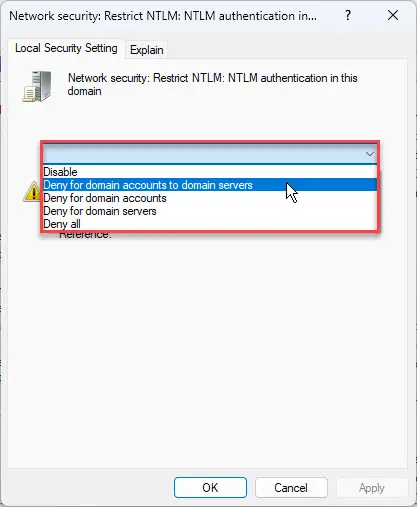
In the right pane open the policy “Network security: Restrict NTLM: NTLM authentication in this domain.”
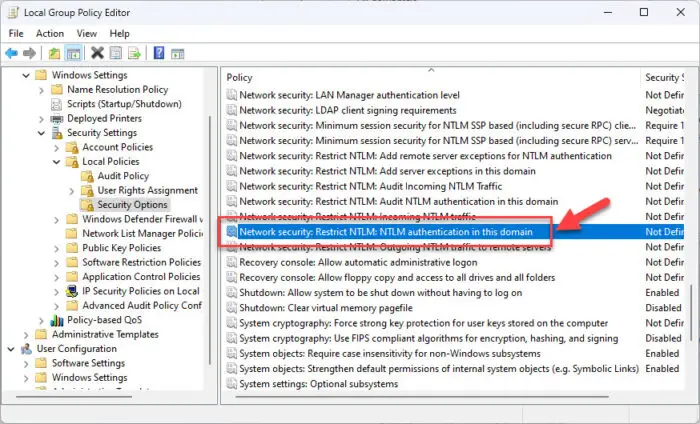
Open the group policy to block NTLM authentication -
Now select one of the following options from the drop-down menu:
- Deny for domain accounts to domain servers – Domain Controller will deny all NTLM authentication logon attempts to all servers in the domain that are using domain accounts.
- Deny for domain accounts – Domain Controller will deny all NTLM authentication logon attempts from domain accounts.
- Deny for domain servers – Domain Controller will deny NTLM authentication requests to all servers in the domain.
- Deny all (recommended option) – Domain Controller will deny all NTLM pass-through authentication requests from its servers and for its accounts.
Disable NTLM authentication -
Click Apply and Ok.
-
Run the following cmdlet in an elevated Command Prompt to enforce the policy changes:
GPUpdate /Force
Enforce policy changes
All NTLM authentication will now be blocked and the user will be prompted with an error. However, this will block all authentication that uses the NTLM protocol. If you want to authorize the apps that were using NTLM for authentication, then you must shift them to Kerberos.
Closing Words
When an outdated technology is still supported, it does not necessarily mean that you should adopt it. The NTLM authentication protocol is one such example. It is only there to ensure that the apps that are still using this technology continue to work. Otherwise, it has no security significance in today’s world.
Therefore, we recommend that you disable NTLM authentication on your network today and add that extra layer of protection.



