The newer version of Windows 11 has been released for the year 2023, which is 23H2. With this, Microsoft has also published a Security Baseline for this Windows version.
A Security Baseline is an additional set of security enhancements that can be added to the original security protocols already in place in Windows. This is especially useful for companies and organizations that prefer to take more control of their virtual security.
If you are a system administrator, installing a Security Baseline on a Windows 11 computer will add additional options to the Group Policy so you can control and push those settings to other devices on the entire network. You can download and install the Security Baseline using the guide provided below.
Table of Contents
Download Windows 11 v23H2 Security Baseline
The Windows 11 Security Baseline has been released as a component of Microsoft Security Compliance Toolkit 1.0. Even so, you can download only the security baseline. Here are the steps to do so:
-
Open the Microsoft Security Compliance Toolkit page and click Download.
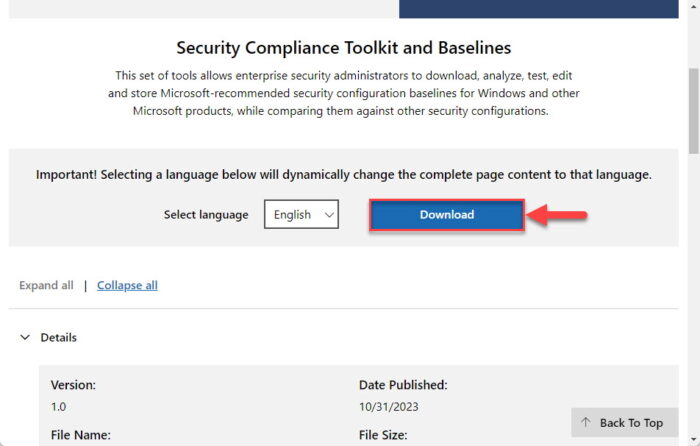
Download the Security Compliance Toolkit -
Scroll down and check the box next to “Windows 11 v23H2 Security Baseline.zip” and click Next.
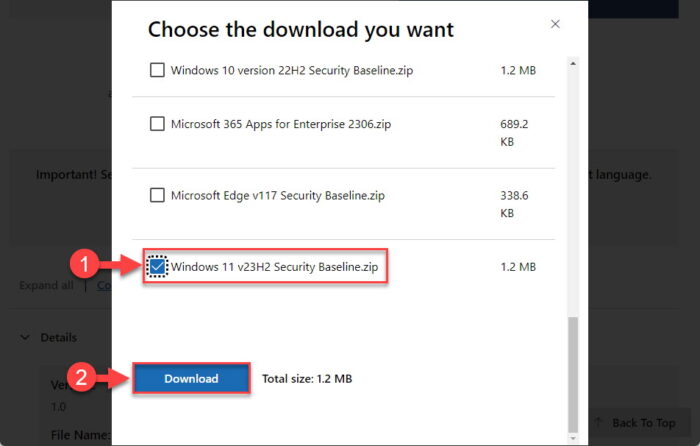
Download Security Baseline for Windows 11 23H2 Windows 11 23H2 Security Baseline will now download. Since it is only 1.2 MB, it should be downloaded instantly.
-
Once downloaded, extract the content of the zip file to a folder.
-
Now navigate to the extracted folder using File Explorer and open the Scripts sub-folder.
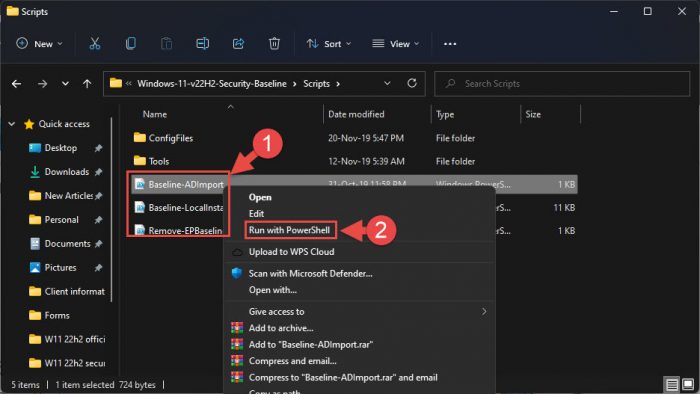
Run scripts with PowerShell The scripts will now run automatically. Wait for the PowerShell window to close on its own.
-
Right-click “Baseline-LocalInstall” file and then click “Run with PowerShell.”
Note: If you are a sysadmin and want to import the new policies to the Active Directory, then run “Baseline-ADImport” with PowerShell instead.
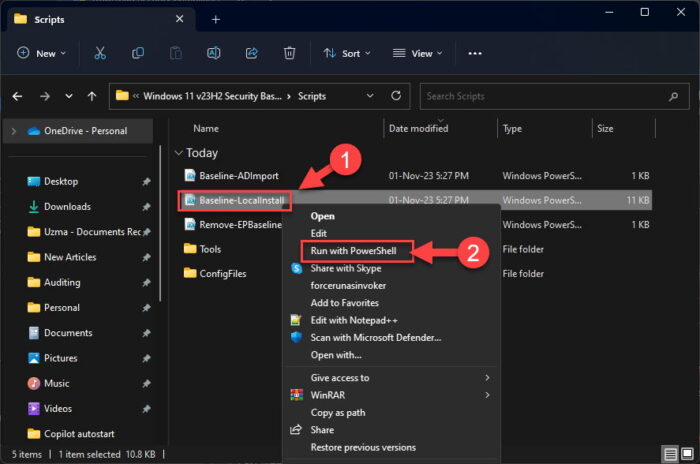
Run the Windows 11 23H2 Security Baseline for local machine -
If asked for confirmation, enter “R” to run the PowerShell script.
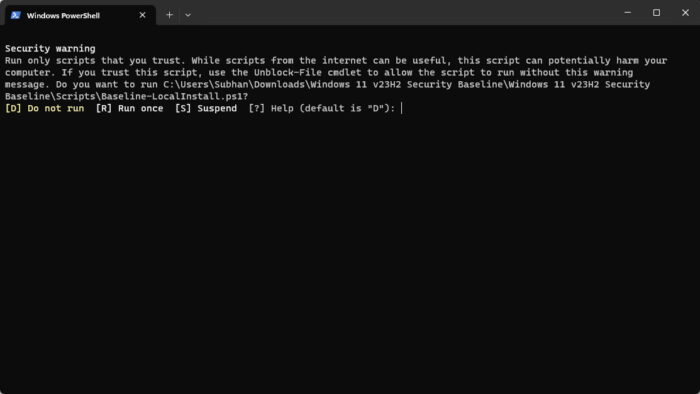
Confirm running the Security Baseline
When executed, the Security Baseline will be successfully installed.
Let us now discuss what the Windows 11 23H2 baseline brings to the table.
New in Windows 11 23H2 Security Baseline
Bringing back Local Administrator Password Solution (LAPS)
LAPS is a feature that lets administrators manage the passwords of the local Administrator accounts of the computer on their network. Passwords are randomized and stored in Active Directory (AD), protected by ACLs, so only eligible users can read it or request its reset.
Microsoft had earlier deprecated the legacy version of LAPS on 23 October 2023. However, they have now moved the newer controls for LAPS natively inbox and its settings under Administrative Templates/System/LAPS within the Group Policy.
Additionally, the following 3 settings have been configured:
| Policy | Default setting |
| Configure password backup directory | Enabled: Active Directory |
| Enable password backup for DSRM accounts | Enabled |
| Enable password encryption | Enabled |
For the backup directory setting, Microsoft has selected the option to backup to Active Directory as the baselines are already targeted as such.
X.509 Certificate Padding
The X.509 certificate is used to manage the identity and enhance the security of the devices on the network with digital signatures. Microsoft has now reintroduced padding for this certificate with the policy “Enable certificate padding.”
This setting affects Portable Executables and should be tested before implementation to a more secure state.
Additions to Microsoft Defender
Microsoft has added the following 10 settings and their default configurations to Microsoft Defender in this Windows 11 23H2 Security Baseline:
| Policy | Default setting |
| Configure local administrator merge behavior for lists | Disabled |
| Control whether or not exclusions are visible to Local Admins | Enabled |
| Turn off routine remediation | Disabled |
| end file samples when further analysis is required | Enabled: Send all samples |
| Configure monitoring for incoming and outgoing file and program activity | Enabled: bi-directional |
| Monitor file and program activity on your computer | Enabled |
| Turn on process scanning whenever real-time protection is enabled | Enabled |
| Scan packed executables | Enabled |
| Enable file hash computation feature | Enabled (as long as Microsoft Defender for Endpoint is deployed) |
Other changes
The following changes have been made with Windows 11 23H2 Security Baseline:
- The MSS Legacy custom administrative template titles were changed to remove the recommendation from the actual setting name.
- The “Audit Sensitive Privilege Use” is being changed to success only (removing failure) from the baseline.
Moreover, Microsoft also reminds the users to configure the Controlled Folder Access policy and enable Tamper Protection.
This concludes all the new security enhancements in Windows 11 23H2 Security Baseline. You can read more about these improvements in the Windows 11 23H2 Security Baseline Release Notes.
Ending thoughts
With every feature OS update, Microsoft releases a new Security Baseline so that enterprises and individual users can secure their systems as per their needs. Similarly, the Windows 11 23H2 security baseline was released alongside the Windows 11 23H2 so that when the enterprise systems update to the latest version, their computers are not left vulnerable to exploits.
We highly recommend that you download and install Windows 11 23H2 Security Baseline regardless if you are a sysadmin or a private user. It will allow you to enhance your digital security and give you more control over it.



