Key Points
- Microsoft has published a PowerShell script that patches the BitLocker encryption bypass vulnerability CVE-2024-20666.
- After running the script, you no longer need to install KB5034441 on Windows 10.
- The Windows Recovery Environment (WinRE) partition no longer needs to be resized.
Alongside the Patch Tuesday update for Windows 10 for January 2024, Microsoft also rolled out an emergency security update KB5034441 that addressed the CVE-2024-20666 vulnerability which allowed attackers to bypass BitLocker encryption from the Windows Recovery Environment (WinRE).
However, when attempting to install this security update, users were met with the error stating “There were some problems installing updates, but we’ll try again later” accompanied by the error code “0x80070643.” This would leave the users unable to install the KB5034441 update and leave their devices vulnerable to the BitLocker encryption bypass flaw that allows access to encrypted data.
For this, I provided a very complex yet functional solution that fixed the issue. The insufficient partition size of the Windows Recovery Environment caused the error, wince the WinRE image file could not be mounted, and you had to delete the WinRE partition and create a new one manually. Once the issue was fixed, KB5034441 was installed successfully, and the vulnerability was patched.
Even after providing the solution, it was so complex that users often missed the steps, or encountered different errors while performing them and could not mitigate the error.
Thankfully, the mighty Microsoft has published a PowerShell script that automates the complex process for you. With this script, you no longer need to install the update KB5034441. Instead, the script patches up the vulnerability directly. You only need to specify the path for a Safe OS Dynamic Update (Compatibility Update) package which can be downloaded from the Microsoft Catalog, and the rest will be taken care of on its own.
Once you use the script to patch the BitLocker encryption bypass vulnerability, you will need to use Microsoft’s Show or Hide tool to prevent KB5034441 from installing anymore, so that Windows Update won’t keep trying to install it forever.
How to use Microsoft script to patch BitLocker encryption bypass vulnerability
Microsoft has provided 2 scripts that you can use to automate the patching of the BitLocker encryption bypass vulnerability. One script is for Windows 10 version 1909 and earlier, and the other is for Windows 10 version 2004 and later. this fact only changes the script syntax, while the rest of the steps remain the same.
These are the steps the scripts follow:
- Mount the existing WinRE image (WINRE.WIM).
- Update the WinRE image with the specified Safe OS Dynamic Update (Compatibility Update) package available from the Windows Update Catalog. it is recommended that you use the latest Safe OS Dynamic Update available for the version of Windows installed on the device.
- Unmount the WinRE image.
- If the BitLocker TPM protector is present; reconfigure WinRE for BitLocker service.
You can use the following steps to use Microsoft’s script to automatically patch the BitLocker encryption bypass vulnerability:
-
Start by downloading the right Safe OS Dynamic Update (Compatibility Update) package from Microsoft Catalog for your specific Windows version.

Download the safe OS dynamic update package -
Now open the Microsoft guide and copy the correct PowerShell script suited for your OS version.
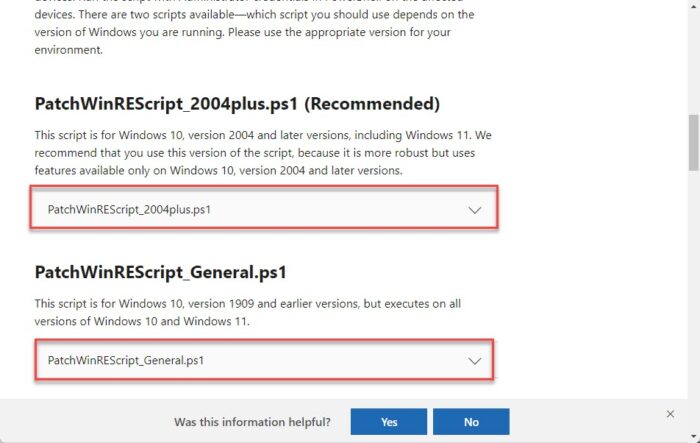
Copy the PowerShell script -
Open Notepad on your PC.
-
Paste the script.
-
Click File and then click “Save as.”

Save as script -
In the Save as window, select “File type” as “All files.”
-
Enter a name for the file followed by “.ps1” extension.
-
Click Save.
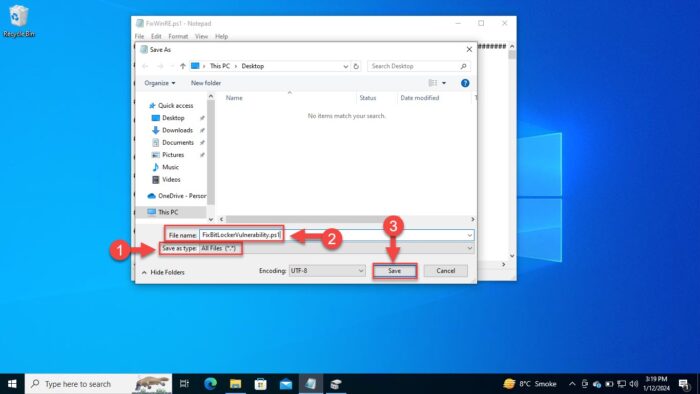
Save file as a PowerShell Script -
Right-click the PowerShell script file and click “Run with PowerShell.”
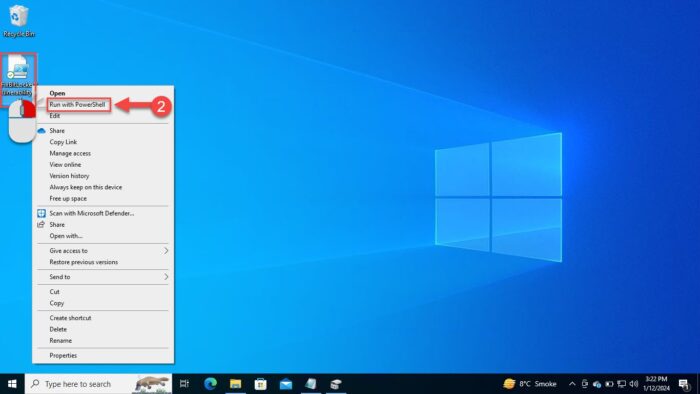
Run PowerShell script -
When asked for the package path, provide the complete path and name of the Safe OS dynamic Update package, along with the file extension, as in this example:

Provide path to Safe OS update package The script will now keep running for a while and patch the BitLocker encryption bypass vulnerability.
-
Once patched, continue to download Microsoft’s Show or Hide Update tool.
-
Run the tool and select “Hide updates.”
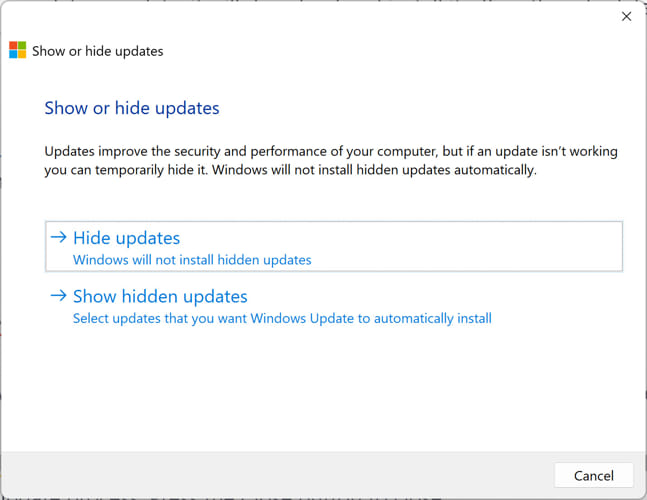
Hide updates -
Select the update “KB5034441” and click Next.
This automatically hides the update from Windows Update and Windows Update will not attempt to install it any further unless you explicitly “Unhide” it.
Takeaway
After performing the steps above, the BitLocker encryption bypass vulnerability will be patched, all without having to install KB5034441, or altering the Windows Recovery Environment.
This is possible because of the user feedback and Microsoft’s response to severe complaints about the update.
Although 3rd party scripts and solutions were available to make changes to the WinRE, they could not be trusted or did not include the complete steps to get the task done without any consequences. Now, you can use Microsoft’s own solution and prevent your PC from falling victim to attackers who exploit known issues.




1 comment
Jeff
Microsoft (support.microsoft.com) reported that KB5034441 required 250 MB of free space in the recovery partition to run the update successfully. Disk Mngt on my system reports that it has 499 MB of 100% free space in the recovery partition, yet this update continued to fail. Suspected reason is that this partition is uncharacteristically, in my case, located in front of C:, but don’t really know if that’s it.
Ran through Mr. Zafar’s powershell procedure. Guess there is no way to confirm that the patch is installed but it ran very quickly and gave no errors. The only problem was with step 11 concerning the wushowhide tool. Guess security didn’t allow it to download. Searching elsewhere, found this also was a reported problem. Somehow found a link that when placed directly in the address bar downloaded! The .cab file is only 48KB. Ran it, but first did not find KB5034441. Ran Windows Update again and it found and failed it as usual. Ran ShowHide and now it found it– was able to hide it. All appears good. Thank you Subhan and Itechtics.
Don’t hold your breath for a fix from MS. Am expecting that many, perhaps most users with this problem will unfortunately remain vulnerable.