If you find something suspicious on your Windows PC, it may be possible that it has been tampered with in your absence, or someone has manipulated it remotely. It is vital that you keep track of the usage history on your Windows computer so you are aware when someone has gained unauthorized physical or remote access.
Unprotected computer accounts or user accounts with predictable passwords make it easier for people to access your computer without you knowing about it. However, in such an event, you must investigate if and what changes are made to your computer. That can be done by taking several preemptive and investigative methods.
These methods are also useful for parental controls so you always know what your children are doing when on the computer.
In this post, we are going to discuss how you can check the logged Windows history to verify whether someone had gained access to your computer.
Table of Contents
An unauthorized user may have made different kinds of changes to your computer. To check what has been done, you can track different kinds of activity, such as tracking internet usage history, checking any deleted files or folders, checking for recently-editing data, or checking when the computer was booted the last time.
If you suspect that someone had recently gained access to your computer, perform all of the following tasks to get the access details, and also be able to track even more data if it happens again in the future.
Check Browser History
If someone has been meddling online using your computer, then surely they must have left a trace of it. To check which websites have been visited on your computer, you must check the online browser history for each browser, like Microsoft Edge, Google Chrome, Mozilla Firefox, Vivaldi, Opera, etc.
Below you’ll find the different methods to access the browsing history of different web browsers:
Note: You can use the CTRL + H shortcut keys on most web browsers to view the browser history, as opposed to the methods given below.
-
Google Chrome:
- Click on the ellipses (3 dots) in the top-right corner of the browser.
- Expand History, and then click History again.
- Chrome History will now open in a new tab and you can check all of the previous web pages visited arranged through time.
-
Microsoft Edge:
- Click on the ellipses (3 dots) in the top-right corner of the browser.
- Now click History.
- You will now see the History pane on your current tab. If you want to open it in a separate tab, click on the menu button of the History pane (3 dots) and then click Open history page.
-
Mozilla Firefox:
- Click on the menu button (3 lines) in the top-right corner of the browser.
- Now expand History.
- Here, you will see the browser history in the scrollable pane. If you want to view it in a separate window, click Manage History at the bottom of the pane.
Note: Using the CTRL + H shortcut keys will open the History pane on the left side of the current tab.
-
Vivaldi:
Click on the History (Watch) button from the left menu of the browser. This will open your browser history inside a pane on the left.
If you use the CTRL + H shortcut keys, it will open the browser history in a new tab.
-
Opera:
Click on the History (Watch) button from the left menu of the browser. This will open your browser history inside a pane on the left.
If you want to open the browser history in a separate tab, then click Open full History view from inside the History pane.
Using the browser history, you can determine when a specific webpage was accessed. This will let you know if someone had accessed your PC without you knowing.
That said, someone who accessed your PC with a malicious attempt can also be smart enough to remove their footprint y deleting the relevant browser history, in which case, you may not be able to determine if and when your PC was used to browse the web.
Check Windows Events
Both Windows 10 and 11 track and store user activity (if enabled). This is also the default Windows setting. Thus, you can check when your computer was last powered off and powered on.
To check the last time your Windows PC was powered on or off, you need to use the Event Viewer. The Event Viewer records all events occurring on your machine, including the details for any errors, BSODs, power states, etc.
Follow these steps to check when your PC was powered on and off:
-
Open the Event Viewer by typing in eventvwr.msc in the Run Command box.

Open Event Viewer -
From the left pane of the Event Viewer, expand Windows Logs and then click System.
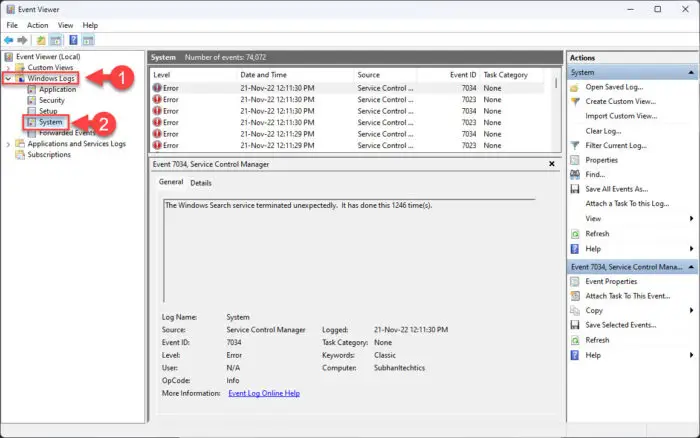
Open system logs -
Now click Filter Current Log from the right-side pane.
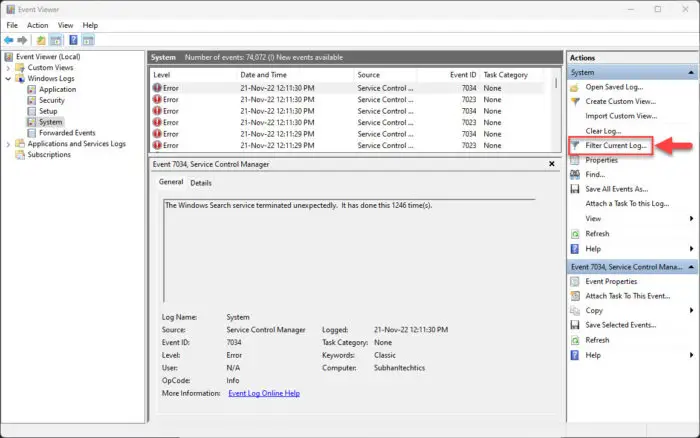
Filter logs -
From the filter window, expand the Event sources drop-down menu, scroll down, and then select Power – Troubleshooter. Then click Ok.
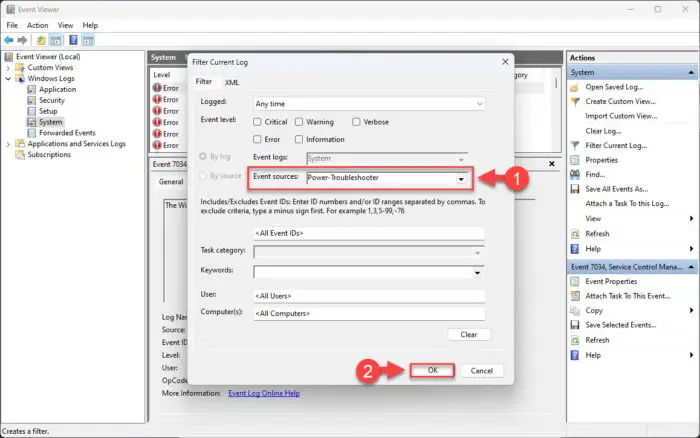
Filter power logs You can now see different entries for system logs for when the computer was put to sleep (shut down) and when it was woken up (booted up) for different dates.
-
Now double-click on the log which seems suspicious to you. You will then be able to see more details about the log entry, stating when the device was powered on and when it was shut down.
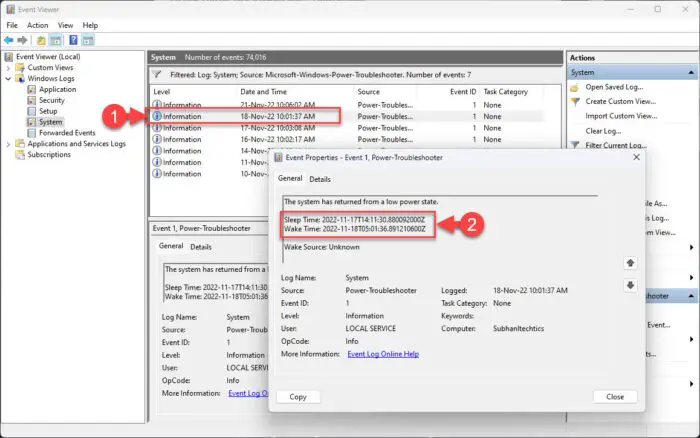
View sleep and wake time of computer
Using the Event Viewer, you can determine if and when your computer was used in your absence.
Using the given method above, you can also monitor other activities on your computer.
Check Recently-Edited Items
Another quick way to check if your system has been in use is to check the “Recent Items” folder, which tells you if anything on your PC has been modified recently. The Recent Items directory stores the links of the files and folders that have been accessed recently, for quick access.
From that list, you must differentiate what you accessed and edited the last time, and what was edited without your knowledge.
-
Open the Recent Items folder by typing in recent in the Run Command box.

Open Recent Items directory -
The Recent Items directory will now open in File Explorer. Click on the Date Modified column header and arrange the items in descending order.

Arrange Recent Items in descending order
Now, you can see what items have been edited and when. You can then open these items and identify any visible differences.
If you do not see the “Date Modified” column header, simply right-click on any header and select Date Modified from the context menu.

Check the Recycle Bin
If a user has manipulated your PC and then deleted any files, you can likely find and restore the files from the Recycle Bin. The Recycle Bin in Windows stores any deleted items for 30 days before automatically deleting them permanently.
Open the Recycle Bin from your desktop, or by searching for it in the Start menu, and then click the Date Deleted column header to arrange the items in descending order.

You can now see what items had been deleted from your PC and when.
Note that it may be possible that the person who gained unauthorized access may have permanently deleted the items or emptied your entire Recycle Bin, leaving no trace of any activity at all.
Preemptive Measures to Check Recent Activity on Windows
If you are suspicious that someone has accessed your computer without your knowledge, then there are better things through which you can determine exactly what they had done. However, for those things to work, you must do some preemptive configurations and installations.
This includes giving your PC permission to track its activity, configure the relevant policies, and install third-party software.
Store Activity History on Device
As we mentioned earlier, by default, the Windows operating system stores the activity history of your computer. However, if the feature has been disabled, here is how you can enable it:
-
Navigate to the following:
-
In Windows 11:
Settings App >> Privacy & security >> Activity History
-
In Windows 10:
Settings App >> Privacy >> Activity History
-
-
Here, toggle the slider or check the box next to “Store my activity history on this device” to enable it.

Store activity history in Windows
Your PC will now locally store all activity history of the machine that you can then view under App Permissions in the Privacy tab inside the Settings app.
Inside each of these permission elements, you can view the Recent activity for the last 7 days and see which app or program had requested it.
Configure Audit Policies
You can also keep track of when a successful or failed sign-in attempt has been on your computer and many other parameters through the Windows audit Security Policies. However, you must first configure these policies so that the Windows OS can start logging them.
This technique is especially useful for sysadmins working inside domains and workgroups.
Follow these steps to configure and enable audit policies on your Windows PC:
Learn how to install the Local Security Policy editor in Windows Home edition.
-
Open the Local Security Policy editor by typing in secpol.msc in the Run Command box.
Open Local Security Policy editor -
Here, navigate to the following using the left pane:
Security Settings >> Local Policies >> Audit Policy
-
You will now see 9 security policies in the right pane. Double-click the first one and then check the boxes next to Success and Failure. Then click Apply and Ok.

Configure the first audit policy -
Now repeat Step 3 for the remaining policies, which include:
- Audit account logon events
- Audit account management
- Audit directory service access
- Audit logon events
- Audit object access
- Audit policy change
- Audit privilege use
- Audit process tracking
- Audit system events
-
When all of the policies have been configured, run the following cmdlet in an elevated Command Prompt to implement the changes:
GPUpdate /Force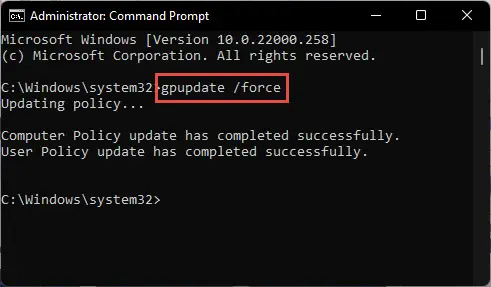
Enforce Group Policy changes
Use Keyloggers
Keyloggers are software that record and store the keys pressed on your keyboard and mouse. These are usually used for malicious purposes, but you can use them to your advantage and keep track of what activity has been performed on your PC.
These tools are excellent for parents so they know what their children are up to once they are off the computer.
There are different types of keyloggers available today. There are even some that also record other activities, such as video and audio calls, spying through the device’s microphone, email data recording, and much more.
Here is a list of a few keyloggers that we believe would benefit you:
Once a keylogger is installed, you can then occasionally monitor if anyone has accessed your PC behind your back.
Closing Thoughts
Even though there are measures to check and track the usage history of a Windows computer once any malicious activity has already taken place, the information might not be very detailed, especially if the user was smart to remove their footprint.
This is why we recommend to our audience to take precautionary measures and secure their systems in every which way they can, which includes setting up complex passwords, using Windows Hello, configuring backups, and of course, taking the necessary measures to limit access in case of a successful break in.



